|
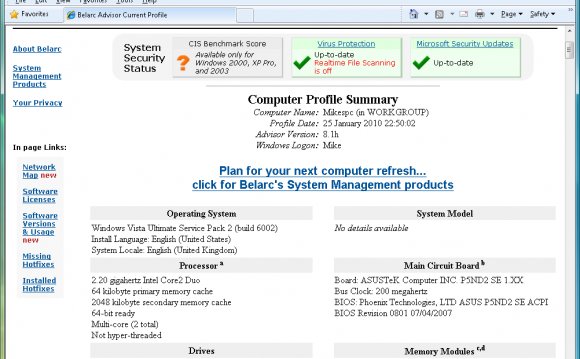
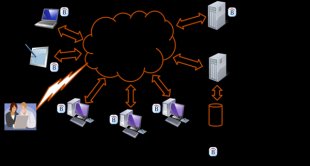
Belarc's cloud architecture enables customers to simplify and automate the treating of all their desktop computers, servers and laptops around the world, utilizing a single database and Intranet server. BelManage instantly produces a precise or more-to-date central repository (CMDB), composed of detailed software, hardware, and security designs. Click the link to determine a brief video about how BelManage works.
Our items can be used for software license management, configuration management, cyber security status, information assurance audits, IT resource management, and much more.
Belarc's items let the following functions with an enterprise-wide basis:
Resource Management
- Software license optimisation with automatic discovery of installed programs and suites, software license secrets, software usage data. Belarc's Data Statistics module offers as they are certification for those major suppliers items including complex server and desktop software from Oracle, IBM, Microsoft, Adobe, ESRI, AutoCAD yet others.
- Server virtual machine dependencies. BelManage instantly finds out the virtual machines and dependencies towards the physical hosts for VMWare, Microsoft and lots of Linux virtual operating-system conditions. This selection also enables you to definitely instantly see each time a new VM instance is produced any place in the enterprise.
- Server software discovery. BelManage instantly finds out the particulars of installed and used server software for example Oracle database and programs, Microsoft SQL Server, IBM database and programs, and much more. BelManage supports Home windows, Linux and Solaris (x86) server os's.
- Operational CMDB. BelManage instantly produces an current, accurate CMDB, with CIs and dependencies for those host machines, installed software, and network attached products for example network ink jet printers, IP phones, pills, mobiles along with other products.
- Software Catalog. BelManage instantly normalizes the discovered configuration data and fosters an application Catalog of approved and never approved software by version and group.
- Hardware &lifier software upgrade planning
- Identify unused, unlicensed, unauthorized, obsolete software
- Enterprise sights from it opportunities
Configuration Management
- Approved and unauthorized programs by versions.
- Change History. BelManage instantly tracks hardware and software adds and removes
- Automatic comparison to plain images
Security
- Missing Microsoft, Adobe, Oracle Java, etc. security patches, service packs, and DoD IAVA status
- NIST security designs (BelSecure)
- Anti-virus status
- Approved and unauthorized network attached products (including mobiles)
- USB storage use by approved and unauthorized products.
Service Desk and Procedures
- Current accurate designs
- Hardware and software adds and removes
- Server and application consolidations
- Variance from standard images
- Hard disk drive free space and Wise status
Audit
More details
For .
|